Edit: Picture is not reflective of anything… I just thought it was funny.
Edit: Picture is not reflective of anything… I just thought it was funny.
I came across an article in my feedly (yes, I use feedly – mock all you want, but I like the interface) about Let’s Encrypt. If you haven’t heard about Let’s Encrypt, it’s a certificate authority – a free, automated one that gives X.509 certs for use to secure TLS sites. SSL too I suppose, but let’s assume you’re not using that anymore because that would be foolhardy nowadays. So you’re not doing that, right?
Anyway the article, which in my opinion is astute and worth a read, cites issues around certificate issuance and points to potential issues associated with the public PKI we have today – or at least the de facto implementation that exists right now. But I think the problem is actually bigger than what the article lays out. It’s not difficult to see why, but let’s break it down anyway.
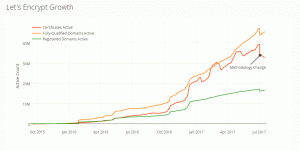
First, the growth of Let’s Encrypt. You might find it interesting to learn that Let’s Encrypt, launched a little over a year ago, is now the biggest CA by volume. It’s pretty spectacular actually. Check out their growth trajectory since they launched about 18 months ago:
If you’re surprised by this, you shouldn’t be. Why not? I’ve written about this before, but it absolutely jives with the economics of how certificate authorities work. Which leads us to the second point: the economics of PKI.
Here’s the deal: these aren’t complicated. And there’s a very precise place that market dynamics lead. On the costs side, there’s what goes into setting up the CA: things like buying an HSM, securing equipment, building processes, writing a Certificate Policy, etc. In terms of ongoing costs, there’s the maintenance costs associated with operating it such as hosting, customer service, revocation, bandwidth, etc. etc. It also by the way includes the security controls and countermeasures that go into defending the environment, hardware, software, etc. So the costs, in large part, correlate to the security services provided. It’s not a direct one to one – it’s not necessarily that the more you spend, the more secure the process is (after all, there are certainly things like economies of scale and efficiency that can play a role here.) However, it’s a loose barometer – the more you spend, the more secure your CA tends to be.
On the revenue side, certificates that you sell (or in this case give away for free) drive revenue – the exception being Let’s Encrypt and other CA’s that have figured out a way to provide the service for free (i.e. being offset by donations, consulting services, or something else). Competition among CA’s is high and they differentiate almost entirely on price because people will buy whatever’s cheapest (since the underlying differences between them – such as the security that goes into providing the offering is invisible to the purchaser). So how do certificate authorities (commercial ones anyway) increase revenue? There’s pretty much only one way: cut costs. What costs are they cutting? As we discussed above, the things that (on the whole) provide security to the system: things like controls & countermeasures, administrative costs associated with keeping the environment secured, revocation infrastructure, etc. So long as CA’s meet the minimum floor provided by the browser folks (i.e. the minimum requirements list required for them to operate) and pay the browser folks the money to be included in their trust store, purchasers do not care.
The upshot of this is that the security of the model will degrade over time as CA’s carve off more and more to drive up revenue (continuing that they meet of course, the absolute minimum requirements to stay accepted by the browser community.) It’s written in the stars market dynamics that this will occur and we’ve seen it borne out over the years. So how does a free certificate play in that world? A few ways. In the short term, it causes downward price pressure on the CA’s that are already playing close to the wire. This, in turn, leads to reductions in their ongoing operational costs. Which, probably isn’t great (again, short term.) Second, maybe it causes “shedding” of commercial CA’s from the business – they literally can’t compete with free, so the old guard exits or gets clobbered.
It also could be good long term. Maybe it encourages sites that would not otherwise be able to afford using TLS to do so. That’s worthwhile – provided a few things happen. Specifically, the minimum standards need to be real – they need to have teeth, not suck, and be reflective of what security the process actually needs. Let’s put it another way, the danger is that the certificates economic forces are driving down what CA’s can offer down to the minimum floor of what’s acceptable. That really, really isn’t good unless that floor is legit. Who sets this? Well, technically each browser, OS, application, or other vendor can set their own – but in practice everybody pretty much toes the line of the Baseline Requirements set by the CA Browser Forum. You can see a handy list of the specifics for inclusion of the most relevant OS/Browser folks on a page they maintain here: https://cabforum.org/browser-os-info/. It’s a community effort, consisting of most of the major CA’s out there and a number of the relevant members. So, community consensus drives it. That’s OK as far as that goes, but it bears saying that there’s a potential conflict of interest that the community needs to be careful about.
So, bottom line: we’re looking to you CA Browser Forum, to keep the baseline requirements reasonable. Seriously.